Community articles — Reports
Write up experiments and research with LaTeX templates for project and lab reports—including layout guidelines to help guide you through the writing process.
Recent

Práctica Laboratorio de Materiales aeroespaciales No. 1: Caracterización y análisis de estructuras cristalinas

The complete business report acts as proposal ending with a decision on whether the idea is viable or not. A positive conclusion will lead to a suggestion of further investigation within this field. Present day wind turbine faces plenty of maintenances, issues and blade failures, all these problems together are difficult to handle and thereby very costly. That is why this report aims to come up with an idea solution to detect manufacturing errors and faults before installing the wind turbine blades. This business report aims to investigate whether a Manufacturing Scanner has the ability to detect errors and faults in new wind turbine blades. In addition the business report examines if the idea based on a Net Present Value calculation along with a budget is economically beneficial. The business report includes a technical description of an x-ray scanner, materials in wind turbine blades and software detection of anomalies. A business plan is conducted to determine whether the Manufacturing Scanner is a viable business opportunity. The business plan consists of a market analysis, which includes a supply chain, positioning, pricing and customer segments, and furthermore a budget, including a Net Present Value and business case. Based on the investigated areas and the final conclusion, the idea seems viable. The scanner is possible to produce at a reasonable price, the project is economically beneficial and there is a present market potential.

With rapid electrification of transportation , it is becoming increasingly important to have a comprehensive understanding of criteria used in motor selection.For that design and comparative evaluation of interior permanent magnet synchronous motor ,induction motor and switched reluctance motor are needed.A fast finite element analysis (FEA) modeling approach is addressed for induction motor design.Optimal turn off and turn on angles with current chopping control and angular position control are found for Switched Reluctance Motors (SRM).Noise Vibration and Harshness (NVH) analysis are done using workbench ANSYS analysis.Simulation and analytical results show that each motor topology demonstrates its own unique characteristics for Electric Vehicle / Hybrid Electric Vehicle.Each motor's highest efficiency is located at different torque-speed regions for the criteria defined.Stator geometry ,pole/slot combination and control strategy differentiate Noise Vibration and Harshness performance.
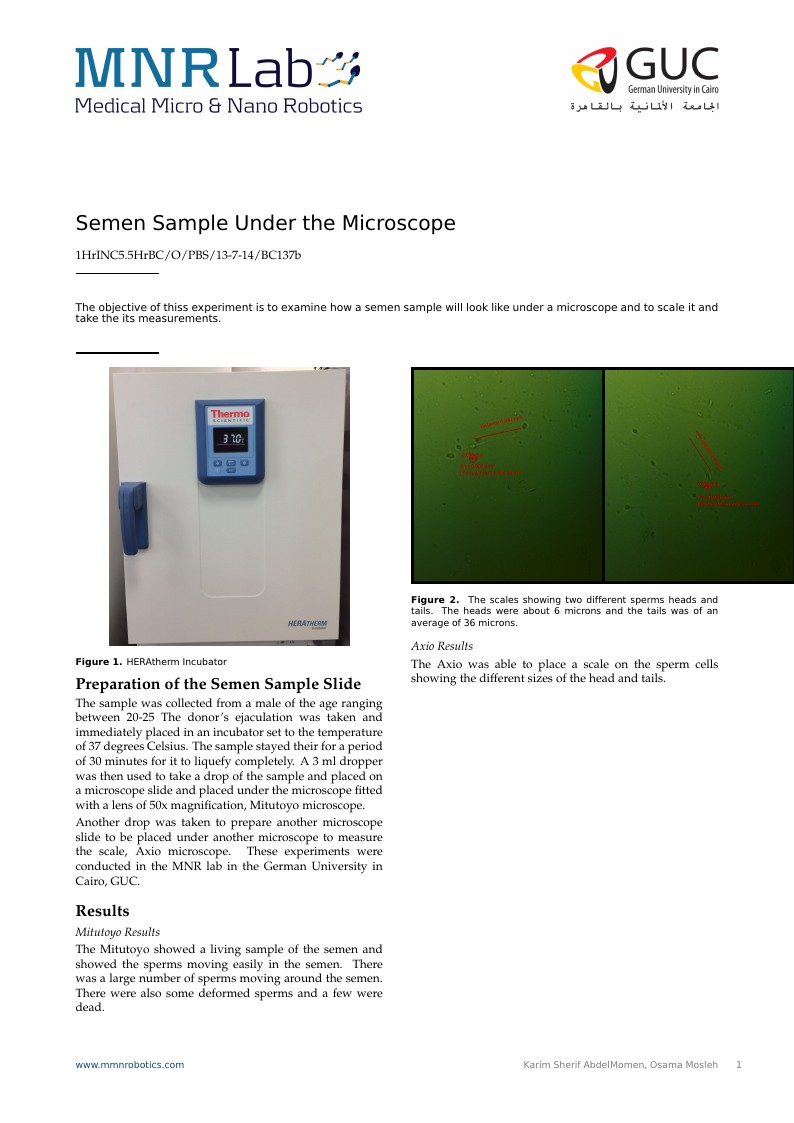
The objective of thiss experiment is to examine how a semen sample will look like under a microscope and to scale it and take the its measurements.

Math project.

Computer vision systems can be applied to a wide variety of tasks, but some of the most interesting are those related with security and surveillance. Within this group, our application for Video Surveillance for Road Traffic Monitoring can be placed. We propose a solution based on machine learning and video analysis techniques that involves the whole process: database evaluation, background estimation, foreground segmentation, video stabilization and object tracking. As a result of this, our system will be able to monitorize some basic parameters of traffic flow as vehicles counting or speed estimation.

Reseña del Autor del premio Nobel

En la actualidad, el estudio y análisis de los sistemas de control automático representan un campo de aplicación bastante extendido, esto debido a las imperantes necesidades por mejorar los procesos productivos, optimizar los recursos e incluso para predecir comportamientos, desde entornos educativos, investigativos o industriales, hasta entornos económicos, sociales y demás. En efecto, esto ha impulsado a los desarrolladores a buscar herramientas o alternativas que permitan aumentar las capacidades de cómputo al momento de desarrollar un sistema de control automático. Ahora bien, la instrumentación industrial desde hace muchos años viene comandada por los Autómatas Programables (PLC), dispositivos útiles e ideales para ejecutar las tareas de control de una planta, independientemente de la escala. El presente documento presenta el diseño e implementación de un controlador PID en una planta didáctica conformada con equipos industriales, haciendo uso de OPC y algunos conceptos de la teoría de control. Mediante la herramienta computacional MATLAB se realiza la identificación de la planta obteniendo su función de transferencia, y haciendo uso de algunas herramientas disponibles en este software, se determinan los parámetros de sintonía de un controlador tipo PID, para posteriormente sintonizar la estrategia de control implementada en un autómata programable de gama alta.

Modelo de proposta de desenvolvimento de software
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.